I was recently talking with my parents, and I saw my dad take out his notebook to find some passwords. “It’s not the same ones that I usually use”, he said.
My mom, she does not have a notebook, she uses the same password. A short, easy-to-guess password.
They’re not the only ones to blame. In my tech career, I saw a lot (and I mean, a LOT) of password bad practices, from using default passwords on sensitive apps or devices, sharing passwords in clear inside email or team communication platforms to even having company passwords written and left in plain sight (type “french tv password expose” in Google Images and have fun).
It’s time to talk about passwords and security!
Your passwords are weak
By the raise of hand, who here uses a password with:
- A date of birth
- The name of your kids
- The name of your pets
- Your favorite band
- Your favorite sport or sportsman
- Your place of birth / wedding / where you met your s/o
And last, but not least:
- Who writes her/his passwords on a Post-it, a document, or a notebook?
- Who uses the same password for several websites/apps?
Don’t be shy in the back, I can see you!
I could continue for a while.
These are not good and secure passwords. Sure, Luke2014 is easy to remember. Let’s look at how long it would take to be cracked:
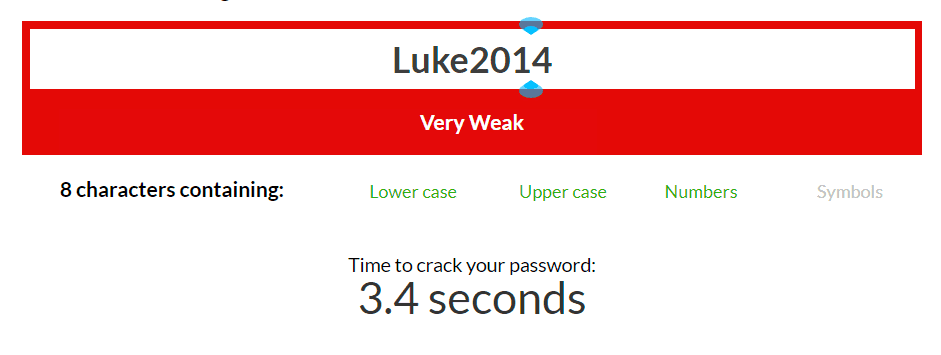
And that, with the current computing power. Imagine when Quantum Computing will be available to hackers…
Oh, and if you think I’m exaggerating when I say people use simple passwords, here are the most used passwords in 2023:
- 123456 (used by 4.5M people !)
- admin
- 12345678
- 123456789
- 1234
- 12345
- password
- 123
- Aa123456
- 1234567890
All these “passwords” are cracked in less than 1 second, and are used by more than 300k people.
Other common passwords are “demo”, “pass”, “secret”, “welcome”, “jesus”, or “minecraft”.
Speaking of Minecraft:
Don’t Leave Social Info Everywhere
People leave a lot of hints when using social media.
Scrolling on Instagram feeds, it’s sometimes easy to get names and ages of kids, pets, favorite places or hobbies, supported sports teams or athletes, etc.
From there, since a lot of people have bad password practices, it’s not hard to brute-force and find “Luke2014”…
Beware of Rainbow Tables
If you want to use this tool or any other of this type, be sure that they don’t store your password and its encryption result. Some websites with dubious ethics used to do that, and feed what’s called rainbow table.
They are later sold on the Dark Web and used to find password correspondence from hacked dumps.
For instance, let’s say you test your password Luke2014. It will be encrypted using several methods, and stored with its hashes in the rainbow table.
MD5: a4a7254cc21d1ffa9488448f295809b9
SHA-1: cbd84e90dccb2671bf3f76233cb2baf5327f2abb
SHA-256: a03bb353162bff2f172ef025bbff1fd369a377a72f409d228e601ae19481f908
etc.
From there, it’s easy to hack into accounts from a leaked database dump.
Name: John Doe; Email: john@doe.com; Password: cbd84e90dccb2671bf3f76233cb2baf5327f2abb
Boom. Done. John Doe is hacked and lost his account on this website.
So what makes a good password
Use entropy
Alright! You’re playing with Luke. Luke has a box of Legos. Many Legos.
He asks you to blindly pick a brick, and guess the color. Of course, the more colors you have, the harder it is to guess which one you picked.
Now imagine that you have to guess the type of brick (let’s pretend you can’t feel it ^^) AND the color.
It’s even more difficult, Luke.
Password entropy is like that. It measures how hard it is for someone to guess your password.
The more different types of characters (letters, numbers, and symbols) you use, the longer your password is (the more “colors” and “shapes” it has).
That’s why a password like “Ab1$xyZ8” is much harder to guess than “1234”, it has more variety and is longer.
If you only use lowercase letters (a-z), there are 26 possible characters.
If you add uppercase letters (A-Z), there are 26 more, making 52 characters.
Add numbers (0–9), and you get 10 more, making 62 characters.
For the maths guys here, this is how entropy is calculated:
Entropy = log₂(Character Set Size^Password Length)
Make it Long
The longer the better. The strict minimum nowadays is 12 characters. A longer password will, logically, take longer to brute force and hack.
For instance, “Luke10062014” would take 21.1 minutes to be cracked (instead of a mere 3 seconds for “Luke2014”. That’s still a bad password!!
Make it Complex
You have to make your password more complex, using a mix of lowercase and uppercase letters, digits, and symbols. If you use uppercase, don’t put them at the beginning or the end, as this is obvious.
Look at how long it would take for a more complex, 12-character password, to crack (and I did not even use symbols!)
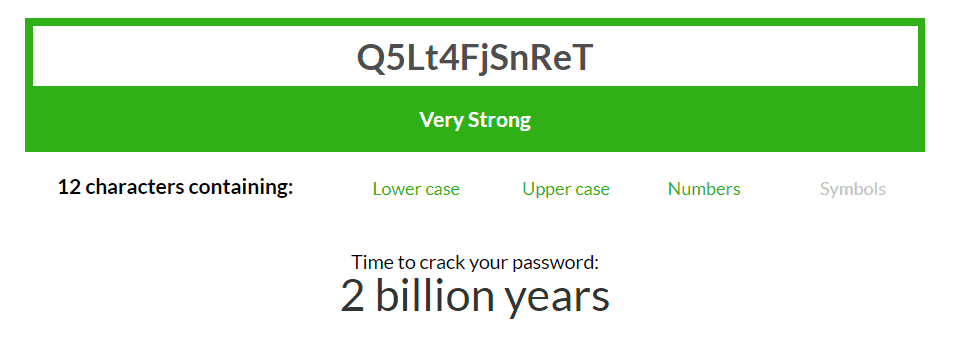
Even when we all have Quantum computers, I’m pretty chilled. (unless it’s in a rainbow table. Password monster states that “Your passwords are never stored.”
Add a pinch of salt
To make passwords even more complex and hard to hack, conscientious database managers often “salt passwords”.
Salt is usually a random set of characters added to the beginning or end of a password, and it’s different for every user. For example:
- User 1: Password is “Luke2014,” salt is “X9@!,” so stored as “X9@!Luke2014”
- User 2: Password is “Luke2014,” salt is “G7$&,” so stored as “G7$&Luke2014”
Each salt is random and unique, so even if two people have the same son’s name and birthdate (and use the same bad password practices) Luke2014, their salted versions look completely different.
This makes it nearly impossible for someone to figure out the original password just by looking at a list of salted passwords.
But how can I remember such complex passwords?
That’s a good question! There are many ways, from using very long, but easy-to-remember passwords, to adding key patterns to your passwords, adding the website/app you use inside, or, even better: using password managers.
Long But Easy to Remember
First, remember that “the longer the better”. If you really want Luke to be part of your password, make it longer, even if you want to use only alphanumeric characters.
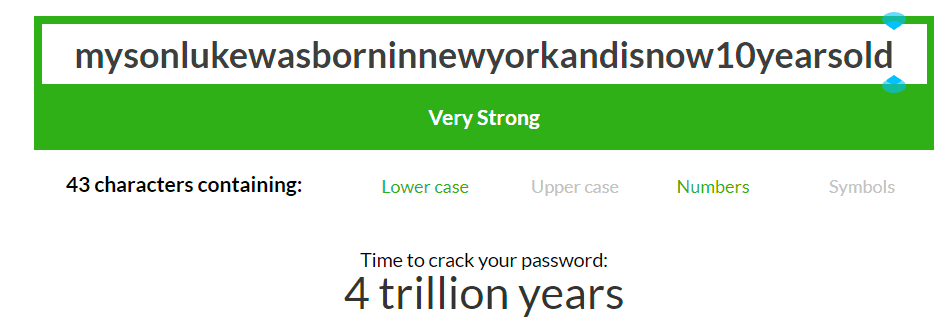
The cherry on the cake: you can even update this password each year!
Let me give you one password I’m sure you’ll still remember by the end of the day: “thewhitehorseisjumpingoverthewoodenfence” will not break before 6 million years.
Use Patterns
To each his pattern. You can for instance add something easy such as:
“qscvgy” before your password, and add “rgbnji” at the end. It will add entropy to your password without adding too much difficulty for you to remember it.
Hint: look at your keyboard 🙂

Use Password Managers
The best, and most secure way, is to use password managers.
Every browser allows you to store passwords. That would allow you to use a different password everywhere.
Be careful though: by default, browsers’ password managers do not encrypt your password, and do not protect them by a master password.
You MUST at least protect your passwords with a strong, secured password that’s stored nowhere else than in your head.
Many tools, free, freemium, or premium make great password managers.
They allow you to:
- Protect your whole vault using a single, “master password”
- generate and store random passwords for each site and app
- store payment details
- auto-login on pages
- ask for your master password for sensitive websites (banks…)
- store secure notes, documents, and personal data
- etc.
Some more advanced ones can even replace apps such as Google or Microsoft Authenticator.
And you can even synchronize all that between your devices (smartphone included), or securely share passwords. (No more clear passwords shared in Slack, Discord, or via email)
Encryption is made “at rest”, which means passwords are encrypted on your devices, and only the encrypted version is stored in the cloud.
Here are a few password managers you can try:
- Bitwarden (free)
- Dashlane (freemium, my favorite)
- 1Password (freemium)
- LastPass (freemium, with an Enterprise version)
- KeePass (free, but only desktop app)
Takeaways
- Use long and complex passwords (at least 12 characters)
- Use a different password for each website or application
- Do not write your password down on a Post-it or a notebook
- If you want to write them on a Word document, secure it with a complex password
- Use password managers, with a strong master password
- Enable 2FA everywhere when it’s available
- Update your passwords regularly
- Avoid using personal information
- Be cautious of phishing
You can read this story by Dr Mehmet Yildiz to learn more about phishing and spam:

No responses yet